It all started when I signed into my crypto account― in an international crypto exchange platform for that matter― to convert my hard-earned coins into USD. As usual, I headed to the sell section of the platform and chose Paypal as my preferred withdrawal method ― I live in Chicago by the way. I then rolled over to the offers section, which was at that time swarmed by a variety of traders offering different exchange rates. On one hand, there were a few traders at the top offering an exchange of 1 USD for 2.03 USD of BTC as at that time ― it kept changing with the crypto market value. However, on a closer scrutiny all were verified. On the other hand, a dozen traders featured the bottom part of the list. Though unverified they offered a higher exchange rate for the same amount of Bitcoin― in this case 1 USD for 1.91 USD of BTC.
So, as fate would have it, I settled for the latter in the hopes of getting a higher return from my exchange. After a few message exchanges, a phone call and a sign-in into an unknowingly malicious link, all my crypto assets went to the wrong hands―And I was left high and dry. Lesson?
Cybercrime is real in the crypto world, especially when carrying out transactions, and it can affect you too. This incident sparked an interest in me to study cybersecurity. As of now, I’m not only certified in the space, but also well versed in its ins and outs.
So, in this post, I will talk about the emerging types of cyber-attacks targeting crypto account holders, how your account can be hacked during a transaction. And what you can do to avoid such scams. Hopefully, this information will help you keep your guard up and avoid being in a similar situation.
Let’s dig right in!
Emerging Types of Cyber-Attacks Targeting Crypto Holders
Stealer malware
Just as the name suggests, a stealer malware is a Trojan (type of computer virus) that collects user information from a computer system without their consent. It typically gathers a user’s vital and confidential information, such as their passwords, usernames and log in information for hacking purposes.
First, you’ll receive a message via email, messaging app or discord account encouraging you to take part in a specific activity to win some reward. For example, participate in beta testing particular software for monetary gains.
The bad news then usually happens when you fall for the bait and click on the provided links. The reason is that they harbor a self-executing compressed file (800M exe) that starts scanning your computer system for important keywords, such as “wallet” for hacking purposes.
Crypto drainer
In a similar vein, a crypto drainer or malware plays out by luring you to a fake crypto web page or ready to go crypto drainer phishing page employing similar tactics to those of a stealer malware, invisible video advertisements on Android devices for example. But this time around, you’ll get an advert on how to generate non-fungible tokens using legitimate third party apps and services, such as Metamask.
However, if you click on the provided links, things will go south, leading you to a phishing page that tears apart your crypto wallet and wipes away the existing balances.
"Crypto drainers are commonly deployed on phishing pages that imitate popular crypto services. Examples of the crypto services that a crypto drainer phishing page might imitate include cryptocurrency exchanges or non-fungible token (NFT) platforms." Report
Some of the recent cybercrimes played out by the stealer malware include the Mars Stealer, idlemaster3d, and Yoyo Game Ltd attacks. Conversely, a perfect example of an infamous crypto drainer website is Pandaverse Mint. Stealer and drainer malware mostly target hot crypto wallet holders. They’re online based, making it pretty easy to glean critical information from them.
How can these two types of malware affect you as a crypto account or wallet holder?
Well, a stealer malware will basically worm into your stored computer system files to collect pieces of information that can help break into your crypto wallet or account. Then send it to hackers for reconstruction to enable entry into your stored digital assets.
DDoS extortion (V2C – victim-to-criminal) cyber-attack
Also known as Ransom DDoS (RDDoS), this cybercriminal activity involves a malicious actor or a criminal group threatening an individual or an organization to part with a given amount of money or crypto assets, or else face dire consequences, for example, a Distributed Denial of Service (DDoS) attack.
In most cases you’ll receive a threatening message about an impending attack on your services unless you surrender to the spelled-out demands. An excellent example of such is the Fancy Bear (APT 28) and Armada Collective (RDDoS) attacks that asked for a ransom of between 5 BTC and 30 BTC beforehand.
A key contributing factor to the rise of RDDoS attacks is the anonymous nature of crypto transactions. You’ll find it difficult to trace the perpetrators once ransom is paid. Not only that, an increase in value of particular crypto currencies, such as Bitcoin, among others has also attracted many, both with good and bad intentions.
“Inevitably, due to the nature of cryptocurrency — that it’s irreversible, anonymous and global — it’s obviously attractive to fraudsters.” Rich Drury, ombudsman manager at the FOS
Address Poisoning Scam: A Sneaky New Crypto Crime to Watch Out For
Address poisoning is a deceptive tactic cybercriminals use to trick unsuspecting users into sending crypto to the wrong wallet. After monitoring public blockchain transactions, the scammer sends a small amount of crypto from an address that closely resembles your recent transaction history — often differing by just a few characters. This cloned address then appears in your wallet’s transaction list, leading users to mistakenly copy and reuse it in future transfers. As a result, your funds end up in the scammer’s wallet, gone forever.
This form of cryptocurrency-related crime is particularly dangerous because it exploits human error and the trust users place in their transaction history. It’s a rising threat in the growing landscape of crypto scams, especially among new users or those engaging in frequent transactions, such as crypto gambling.
To protect your coins, always double-check wallet addresses before transferring funds — never rely solely on past transaction lists.
Cryptojacking
It involves an act of a hacker transferring malicious code to a victim’s device for stealing purposes ― in this case, cryptocurrency assets. This type of attack follows a similar script to that of a stealer or drainer malware manifestation.
In summary:
-
You’ll first receive a malicious link via email, downloaded apps or social media handles prompting you to complete a particular task to earn a reward.
-
Your computer system then becomes infected with a crypto mining code that self-executes on the browser upon clicking on the link.
-
This code then sends your crypto wallet’s details to a hacker’s server for reconstruction purposes. After which, your crypto wallet address becomes replaced by a fake one. This implies that, your future payments via “your crypto wallet” will be redirected to a hacker’s account.
Most non-custodial crypto wallets or hot wallets present prime targets to cryptojackers as they can be interchanged easily. An example of cryptojacking malware is the KryptoCibule virus, usually spread through pirated torrent files.
Note: cryptojacking malware will, in most cases, bog down your device, causing it to lag or operate slowly. Therefore, it’s critical to act with speed to prevent further loss or damage.
Cryptocurrency exchange attacks
They constitute cyber-attacks targeting cryptocurrency platforms, as well as individuals carrying out crypto transactions. Most of them target hot wallets owing to their online nature, vulnerability, and common use in crypto exchanges amongst individuals, and traders.
One way a hacker can gain access to your crypto wallet is by exploiting its private key vulnerabilities. Here, a malicious actor can use their graphics processing units (GPUs) to determine the seed phrase used to create your crypto wallet’s private key. And then develop a similar private key to yours for hacking purposes. A perfect example of such is profanity address hack in which millions of dollars were lost.
Another way of losing your crypto assets is initiating a trade process with a con artist purporting to be a genuine seller or buyer ― like in my case. You can be a victim of such, especially if you’re naïve or are not well-informed about the trending crypto cyber-attacks. In particular, I was new to crypto exchange platforms, so, wasn’t aware of the latest tricks in town used by con artists ― so I ended up losing my hard earned cash.
How my Crypto Wallet got Hacked and How to Prevent it
As mentioned before, selling or buying crypto assets in your favorite crypto exchange platform can turn ugly in a moment’s notice ― Courtesy of the ever increasing number of con artists. And it can be a nasty ordeal so to speak, if anything is to go by my experience.
In a nutshell, here is how it all went down with my faulty transaction
First, I logged into my Paxful account to exchange my earned BTC units into US dollars.
I then headed to the seller/ buyer section to initiate a selling transaction process.
As usual, I choose the preferred payment option. I went for Paypal as it was the most convenient method for me at the moment.
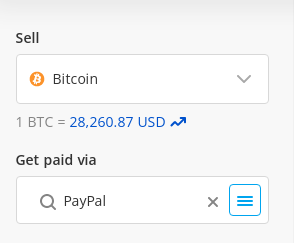
I then proceeded to the corresponding trading page featuring two types of traders: the verified and the unverified ones. For instance, take a look at the following images for better understanding:
Verified traders
Unverified traders
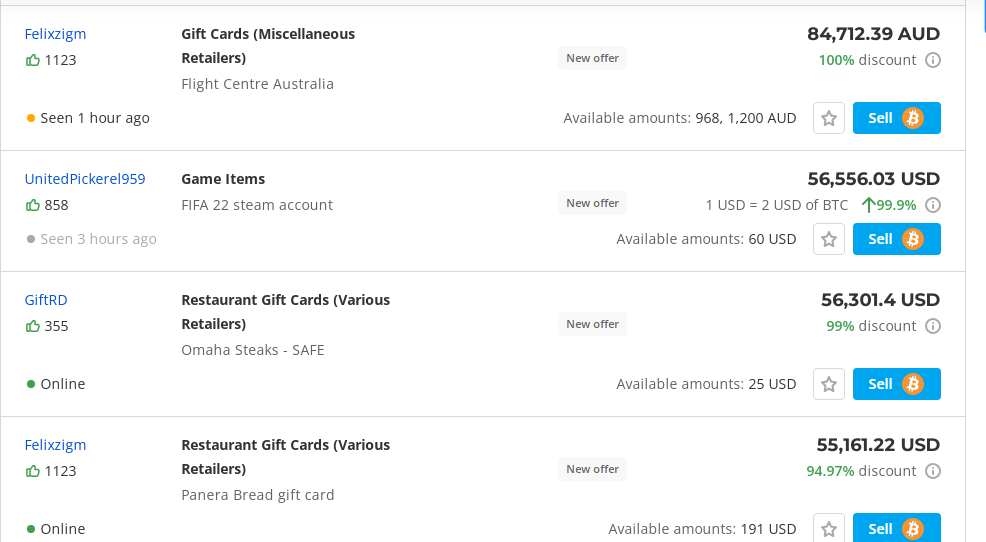
In my case, I chose a trader from the latter group (unverified traders) as they had advertised a higher exchange rate compared to others.
-
So I initiated the trade; and that’s where trouble started.
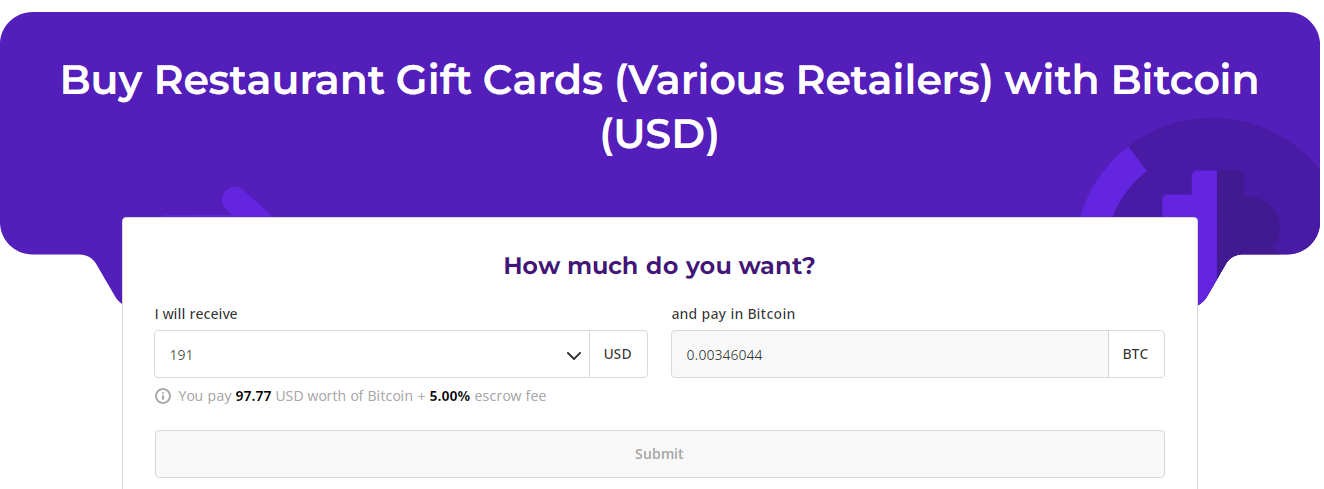
In short, I first keyed in the amount of BTC to sell as usual. I then provided my trading details as it is the norm, my email address in this case. However, things started taking a different turn this time round as I was supposed to get an equivalent amount of USD to the keyed in BTC units in my Paypal account, which wasn’t the case. In fact, the back and forth games with the trader started at this point.
Here is what happened. They initially texted-in to advise that I login to a provided shopify link address in order to access my money as they had sent it there. However, this activity didn’t bear any fruit. The trader then followed up with a falsified customer care message of my crypto exchange platform to my email address to coax me to change my login details to address the problem. Little did I know that things were getting thick; efforts to crack into my account had started. They then communicated back to inform me that I should remove 2FA to allow customer care to resolve the issue now. And that’s how it all went down. The hacker was able to access my account, and within a few minutes, all my crypto assets transferred to another wallet.
Common Ways of Losing your Coins
Having said that, let’s now look at some of the other ways you can lose your crypto assets to cybercriminals ― to avoid my kind of experience:
Not Vetting your Crypto Exchange Partner or Trader
It constitutes the number one “sin” you can commit as a crypto wallet holder or trader on any cryptocurrency trading platform ― whether legit or not. This is because a majority of the current crypto sites have become a haven for con artists owing to the lucrative nature of crypto transactions.
In most cases these shady vendors will flaunt higher exchange rates compared to genuine traders to entice you ― as in my case.
Luckily, it is pretty easy to pinpoint them. You can do so by checking your trading partner’s verification status beforehand. A trader that isn’t verified is a red flag; trade with them carefully if you decide to do so. Otherwise, as a rule of thumb, just go for a verified trader to allow a smooth and successful exchange process.
Not Activating 2 Factor Authentication (2FA)
According to CNBC, crypto hackers are getting smarter by the day, so, having a password as the only gatekeeper for your account can turn disastrous ― a move here and there by a hacker can hand them your account. And this explains my advocacy for 2FA. Enabling it on your crypto account prevents easy access.
For instance, you’ll be required to key in a one-time password sent via email or phone by your crypto exchange platform to gain entry into your crypto account and wallet. That is after inputting your password. So, any Tom, Dick and Harry having your crypto account password without the one-time password wouldn’t proceed anywhere after the initial stage of getting into your account.
To tighten up security, it’s advisable to activate 2FA for all your activities on the account. For instance, when logging in, and before conducting any transaction to prevent most of the blockchain cybersecurity risks.
On-boarding a Rogue Crypto Exchange
Without question, the rise in crypto currency value and transactional profits has led to the mushrooming of crypto exchange platforms. Unfortunately, some of them are fake sites operating in the guise of genuine ones. Signing up on such sites can lead to the loss of your crypto assets or portfolio.
That’s why, it’s super important to determine the authenticity and safety of your go-to crypto exchange platform before making any transactions. You can do so by checking out their legitimacy and customer opinions on review sites, such as Trustpilot and G2. Additionally, ensure that the platform has proper security measures in place. Alternatively, you can sign up with any of the following best crypto exchanges.
Putting All your Eggs in One Basket
Storing all your crypto assets in a single platform is not advisable. You never know what might happen; the site could be hacked, as was the case with FTX. Or you could lose all your assets in a single faulty transaction. And you do not want to end up in court or chasing individuals for your money.
The only effective way to safely preserve your stash is to keep your cryptos Off exchanges or any type of centralized entity. In the event of a bankruptcy due to a large hack or simple mismanagement of the company, you might find yourself "legally scammed" through the dollarization of your crypto holdings at the date of bankruptcy. Add to that 1 to 2 years of US lawyer fees, and you'll end up with much less than the initial loss, not to mention the value of the crypto holdings would have gone up significantly after 2 years.
Decoy Wallet
The safest way to preserve your crypto assets is to allocate them in different wallets and to potentially also have a decoy wallet with a small percentage of crypto holdings in the unfortunate event you are forced by either law enforcement or criminals extorting you with violence.
The $5 Wrench Attack: A Threat to Your Crypto
In the world of crypto, a $5 wrench attack refers to a form of cybercrime where criminals physically coerce someone into revealing their private keys or transferring their coins. Unlike digital hacking or crypto scams, this attack relies on brute force, exploiting the anonymity of cryptocurrency to escape detection.
Crypto gambling platforms and other online spaces often attract individuals holding significant amounts of cryptocurrency, making them potential targets for such threats. To protect your coins, it’s essential to practice good security habits. Avoid openly discussing your crypto holdings, avoid wearing crypto swag and ensure your assets are secured in hardware wallets, multisig wallets that require multiple approvals for transactions.
The $5 wrench attack highlights that cryptocurrency-related crime isn’t always virtual. Staying vigilant and employing physical as well as digital security measures is crucial to avoid becoming a victim.
How to Protect yourself from Potential Cyber-Attacks
As the saying goes, “prevention is better than cure.” implementing appropriate measures to ward off potential or emerging cyber-attacks can ensure the safety of your crypto assets.
Here are some ways you can use to prevent the afore-mentioned cyber threats: stealer malware ands drainer malware
How to protect your account from stealer malware
-
Use Two-Factor Authentication: One primary way of preventing stealer malware is by activating two-factor authentication (2FA) on your crypto accounts. In this case, setting up your normal login password ― which should be a strong one ― in addition to enabling 2FA on your crypto exchange platform’s dashboard. Having two-factor authentication in place makes it difficult for a cybercriminal to access your digital assets even if they have your login credentials.
-
Use of a dedicated password manager: If you find it difficult to memorize complicated passwords for your different user accounts, a password manager can be a helpful tool. It allows you to save unique passwords in an encrypted database eliminating the need to jot down or cram your password.
With a password manager, you can be assured that your passwords will not be easily accessed. It can also automatically sign you into platforms for convenience and help you identify fake websites that may lead you into danger. A password manager can also alert you when you’re using the same passwords for different accounts giving you the opportunity to make changes to keep them secure.
Overall, using a dedicated password manager can help keep different types of viruses at bay, including the redline stealer malware. Examples of the best password managers you can use in 2023 include 1Password, Bitwarden and Dashlane.
-
Continuously update your cybersecurity software: To keep up with the ever evolving stealer malware variants it’s important to consistently update your antivirus protection software. This helps fix any security gaps that may arise and ensures that your system and stored accounts are safe and sound. You can manually update your antivirus program or set it to automatic update mode. Alternatively, you can subscribe to a reliable endpoint solution provider who can manage your updates automatically and take care of all your other needs.
How to protect your account from drainer malware
Visiting suspicious crypto websites or clicking on suspicious links is one sure way of activating the drainer malware and putting your crypto wallet at risk. So, as a rule of thumb, avoid them by all means, however enticing the rewards might be.
In general, keeping cryptocurrency cyber-attacks such as the stealer and drainer malware at bay, requires you to activate the necessary preventive measures from the word go. Having an effective cybersecurity plan or end point solution in place at all times preempts such kinds of malware from infiltrating your system.
DDoS extortion (V2C – victim-to-criminal)
You can prevent this type of cybercriminal activity using two main methods. The first is to install IP protection for small-scale denial-of-service attacks. Protecting your IP by specifying where traffic should come from denies a possible DDoS attack from unwanted quarters. This cuts off cybercriminals intending to flood your system with unwanted details for ransom purposes. To maximize this method, you can extend DDoS protection to all your available IP addresses, internet-facing infrastructure, web services, and DNS servers. This can help seal all the loopholes available to DDoS threat vectors.
Next is collaborating with your Internet Service Provider (ISP) to help prevent the interruption of internet services by any of the attackers. Additionally, provide you with helpful information that can be used by law enforcement authorities in case of an attack.
On the contrary, you can opt for a cloud-based protection service in case of large attacks. In most cases they have all the required resources to counter heavy attacks. For example, they integrate multi-cloud deployment software that takes care of attacks from hybrid cloud deployments and different cloud environments. Plus secondary asset protection software which ensures that all your network’s vital components, such as FTP servers, email servers, APIs and DNS servers are well catered for.
As usual, it’s advisable to install these prevent measures as early as possible to prevent an attack from extortionists wanting a share of your sweat.
Cryptojacking
Keeping cryptojackers at bay is also super important for your digital assets. Some of the preventive measures include installing effective and up-to-date antivirus software or cybersecurity programs. This helps prevent malware from gaining entry into your system. Some of the popular and safe anti-virus programs in the market you can try out include Avira, Mcafee, and Bitdefender.
Besides that, it’s also vital to watch out for the latest cryptojacking trends to help keep up your guard to avoid becoming a cyber-attack victim. This means staying alert on what is going on in the crypto space by reading top blogs, following influencers and keeping tabs on current crypto news.
Another way of slaying the cryptojacking menace is by the use of browser extensions such as minerBlock designed to block out cryptojacking attempts. You can use ad blockers as well, to get rid of those annoying pop-ups and potential malware traffic.
Disabling Javascript on your browser also comes through as a preventive measure; though at a certain degree of inconvenience. For instance, it can cause the breakage of some web pages causing a navigation problem.
Finally, make it a habit not to visit suspicious websites; you can even go a step further by blocking them. My opinion is to visit secured sites for any online transactions: one having an https at the beginning of the URL and not http.
All in all, cryptojacking detection, and prevention using crypto cyber security tools can help safeguard your crypto investments. This makes it important to put in place the necessary preventive measures prior to opening up any crypto account. Besides, conducting cryptojacking detection exercises on a regular basis.
SIM Swapping and How to Protect Against It
SIM swapping is a type of cyberattack where a hacker takes control of your phone number by convincing your mobile provider to transfer your number to a new SIM card in their possession. Once they have control, the attacker can use your phone number to reset passwords and gain access to accounts, including cryptocurrency wallets.
In the crypto space, SIM swapping can lead to the theft of your digital assets. The attacker can bypass two-factor authentication (2FA) that relies on SMS codes and gain access to your accounts by resetting passwords.
|
How to Protect Against SIM Swapping |
|
|
Use app-based 2FA |
Instead of relying on SMS-based 2FA, use app-based authentication methods like Google Authenticator or Authy. These apps generate codes locally and are not tied to your phone number |
|
Contact your carrier |
Ask your mobile provider to add extra security measures to your account, such as a PIN or passphrase, making it harder for someone to impersonate you |
|
Monitor for suspicious activity |
Be alert for signs that your phone has lost service unexpectedly. If you suspect your number has been hijacked, immediately contact your mobile provider |
|
Use a cold wallet |
There is no reason for you to keep any significant funds in a mobile hot wallet, your funds should be safely stored offline |
Cryptocurrency exchange attacks
Finally, you can keep your crypto account or wallet safe from fraudsters by doing the following. First off, is by signing into a crypto exchange platform that has a cold storage feature. This way, your crypto wallet will be stored on an offline mode when not in use, making it less vulnerable to cyber-attacks compared to hot wallets.
The next thing to consider is getting your crypto wallet from a reputable developer who weaves in modern security features on their product. For example, a wallet that doesn’t leave any loopholes in its private keys, supports two-factor authentication and one that automatically logs out after a particular period of inactivity.
Examples of top crypto wallets you can use include the Coinbase wallet, Ledger and ZenGo.
Lastly, you need to vet the person you’re going to trade with. Are they verified? Do they have positive reviews from previous transactions? Doing so reduces the risk of being conned by the ever-increasing con artists, of which there are many on the current crypto exchange platforms.
Social Engineering Scams
Social engineering scams targeting cryptocurrencies exploit trust to deceive individuals into revealing sensitive information or transferring funds. One common tactic involves impersonating governmental agents or customer support agents from exchanges or wallets, contacting victims with urgent account issues. They create urgency to trick victims into sharing login credentials or transferring funds to fraudulent accounts through crypto transfers, crypto ATMs and gift cards.
Another type of scam is impersonating industry influencers, promising unrealistic returns or exclusive investment opportunities via fake social media profiles or direct messages. These scams exploit trust in prominent figures to lure victims into fraudulent schemes, emphasizing the need for verifying information before taking financial actions online.
P2P Crypto & Fiat Triangulation Fraud (Triangle Scam)
In this scam, a fraudster acts as a middleman between a crypto seller and an unsuspecting buyer of a fake product. The scammer lists a fake item online and finds a buyer. At the same time, they initiate a crypto purchase on a no-KYC P2P platform. The buyer of the fake item unknowingly sends fiat to the crypto seller, believing they are paying for a product. Meanwhile, the scammer receives the crypto and disappears. The victim, realizing they were scammed, reports the transaction, leading to potential legal trouble for the crypto seller.
-
How to Protect Yourself
-
Verify Payments Carefully – Ensure the sender matches the buyer’s details.
-
Use Platforms with Escrow – Escrow services help prevent fraudulent chargebacks.
-
Beware of Third-Party Payments – Only accept transfers from the person buying the crypto.
-
Check for Reversible Payments – Avoid methods like PayPal or bank transfers that can be disputed and disclose your identity.
-
Always trade directly with verified buyers to prevent getting caught in this scam.
What to look out for in a Safe Crypto Exchange
When selecting your go-to crypto exchange platform, it’s crucial to look out for the following features to ensure the safety of your crypto assets, both in storage and in exchanges:
Security
This is the number one thing to consider. After all, the platform will be the custodian of your crypto assets, so any security lapse can negatively affect your investments. Check if the site supports two-factor authentication for verification purposes, has a whitelisting feature to highlight the approved participants. And, has a cold storage feature to allow the storage of crypto wallets in an offline mode to prevent hackers from accessing them.
Insurance
Also, check if the platform is insured in case it gets hacked. An insured site can at least give you assurance that you’ll recover your funds if something bad happens. The reputation of the platform is also important. An excellent choice is one that has a commendable number of positive reviews from happy customers. On the other hand, a site with numerous bad or poor reviews from clients should raise your eyebrows.
Reputation
Another thing to look at is the history of the platform you are considering to join. Has it been hacked before? What was the cause and what happened thereafter? Plus, who owns the company? Are they transparent about it? Having answers to such questions can guide you on the next course of action.
Regulatory compliance
Regulatory compliance is yet another worthwhile thing to consider. A well-set cryptocurrency exchange platform needs to have passed the anti-money laundering and know-your-customer checks. This helps keep cryptocurrency privacy issues in check, and the dangers of cryptocurrency cyber-attacks out of the window.
Liquidity
You should also check the liquidity of your preferred site. Does it have enough cash at hand or in circulation to attract more traders and account holders? A site that doesn’t have enough money or digital assets in circulation can lead to trader or customer apathy. As a result, it can go out of business, which is something you don’t want to happen with your digital assets at stake.
Customer support
The level of customer support provided by a platform is also an indication of how safe your investment is. A suitable crypto exchange site should have its customer care service available 24/7 for convenient use. For example, it should allow you to make a complaint or ask a question at any time of the day followed by a quick reply to seek out the issue at hand. In other cases, it should enable you to make timely transactions since crypto prices do change drastically over a short period. A delay in settling your issue can drastically affect your financial possibilities.
Trading methods
Last but not least, take a look at the trading methods used by the platform to determine how safe your transactions can be. Do they transact via ATM, phone, web or apps? Or do they use multiple avenues to transact business? A site with various trading options allows you to choose the most suitable and secure options according to your needs.
How to Check if Your Information Has Been Leaked
Protecting your crypto assets is vital, especially in the face of rising cybercrime and crypto scams. To minimize the risk of cryptocurrency-related crime, it's essential to regularly check if your personal information, including your email, password, and wallet addresses, has been compromised. Several tools can help you detect leaks:
-
Have I Been Pwned: This popular service checks if your email has been exposed in any data breach. It aggregates data from numerous breaches and alerts you to potential risks, helping you protect your coins from being targeted by cybercriminals.
-
DeHashed: A more thorough service that scans various databases to identify compromised information. It also checks usernames and IP addresses, offering an added layer of protection against crypto crime.
-
Firefox Monitor: Built by Mozilla, this tool scans your email address against known breaches and sends alerts, giving you a chance to act quickly and prevent exposure to crypto gambling fraud or crypto scams.
-
Emailrep.io: This tool provides an instant reputation check for your email, alerting you to any risks associated with your accounts.
Key Takeaways
-
Bitcoin theft has become rampant. Therefore, you need to be on constant alert if you’re a crypto wallet or account holder.
-
There is a need for installing appropriate preventive measures to combat Bitcoin crime, amongst other cryptocurrency cybercrimes. Such measures include subscribing to reputable cybersecurity programs, installing effective antivirus software, and constantly updating them.
-
Crypto Crime is becoming more sophisticated by the day. Cybercriminals are now using advanced hacking programs such as the Red Malware ― bought at a fee ― to access a person's crypto account and wallet. So be very careful when visiting suspicious crypto pages, if not at all.
-
It is important to vet a cryptocurrency exchange platform before signing up. This is because there is a rise in rogue crypto sites whose main aim is to defraud subscribers. It is also advisable to check your go-to platform’s security features as they would determine the safety of your digital assets.
-
You can use a variety of methods to protect your crypto account or wallet from cybercriminals. For instance, subscribing to a competent cybersecurity program provider, or installing the required anti-virus program or malware software, among other things.












